SPECIAL REPORT. U.S. intelligence "outsources" cyber-snooping to Israeli-linked firm by Wayne Madsen
As a result of counter-hacking by a "white hat" team of computer hackers, a Milan-based firm, Hacking Team, has been revealed as providing sophisticated hacking tools to the U.S. Federal Bureau of Investigation, the U.S. Drug Enforcement Administration (DEA), and intelligence and law enforcement agencies around the world, including Australia, Azerbaijan, Georgia, India, Panama, and dozens of other countries. Colombia's security agencies actually bought Hacking Team software with funds provided by the DEA.
Leaked Hacking Team documents also point to the firm's software being used to target the computer systems of ABI, Ltd. (Antigua and Barbuda), Barclays, ING Direct, Deutsche Bank, and ABN Amro.
Hacking Team also targeted the computers of Human Rights Watch and Privacy International (PI). Since 1996, this editor has served as a member of PI's International Advisory Board, as well as a contributing editor to the group.Hacking Team founder Christian Pozzi has stated that the hackers who exposed the firm's nefarious activities "will be arrested" and that the company is "working with the police at the moment." Signor Pozzi should realize that by targeting journalists in the United States and PI, it is he and his firm that could face law enforcement action if it should be determined that this editor's computer files, email, or WayneMadsenReport.com has, in any way, been subjected to hacking by his firm or any of its customers.
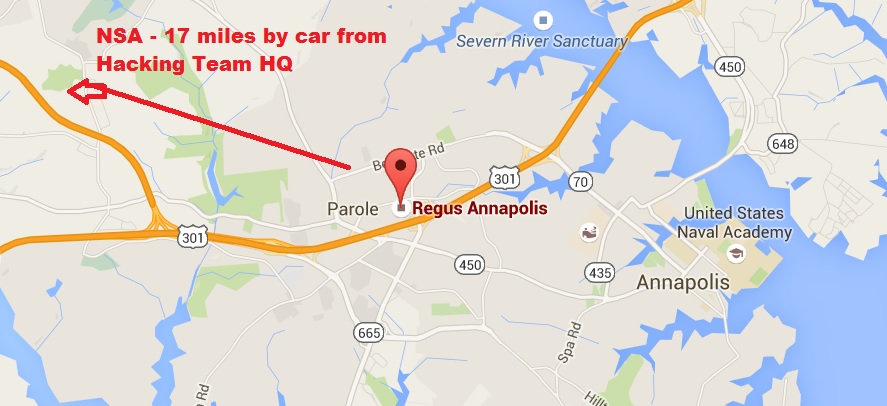
The presence of Hacking Team's U.S. office at 1997 Annapolis Exchange Parkway, Suite 300, in Annapolis, Maryland also suggests that the National Security Agency and its U.S. Cyber Command operation, located nearby in Fort Meade, Maryland, also used the hacking firm's products. In addition to its headquarters on Via della Moscova in Milan, Hacking Team maintains an office at UOB Plaza 1, 80 Raffles Place Level 35-25, in Singapore. In addition, there are reports that the Central Intelligence Agency was also an avid fan of Hacking Team's cyber-snooping software.
Hacking Team is also connected to Israeli intelligence. Its corporate partner, Nice Systems, Ltd., an Israeli software services firm located at 8 Hapnina Street, Raanana, Israel, was connected to some of the Israeli "art students" rounded up by U.S. law enforcement after they were found casing U.S. government facilities and private homes and offices in the months leading up to the 9/11 attack. Nice Systems employees arrested included Tomer Ben Dor (date of birth, 8/24/1975), a former Israeli Defense Force officer, and Michael Calmanovic (date of birth, 9/06/1975), the leader of the Israeli team operating out of Irving, Texas, close to Dallas-Fort Worth International Airport. The Irving team not only included employees of Nice Systems but also the telecommunications billing software firm AMDOCS. Calmanovic rented a mail drop at 3575 Beltline Road in Irving, just a few blocks from the 4045 Beltline Road residence of Almad Khafefa, one of the Saudi suspects in the 9/11 attack.
Nice Systems's chief executive officer is Barak Eilam, a former officer of Israel's signals intelligence agency and NSA's "Third Party" partner, Unit 8200. Nice's president of the Intelligence Solutions Division of the Security Group is Yossi Ofek. One of the Israeli art students arrested in the United States prior was Aran Ofek, identified by DEA as the son of a two-star general in the IDF. Aran Ofek lived with the Mossad cell at Oak Hill Apts. 1913 Estrada Parkway, #259, Irving, TX., and he was arrested by the U.S. Immigration and Naturalization Service on March 26, 2001.
Hacking Team used various code words for its American clients. The DEA was KATIE, the FBI's little-known Remote Operations Unit was called "PHOEBE," and the CIA was known as "MARIANNE." The sale of the Israeli-connected hacking software to such countries as Syria, Sudan, and Pakistan indicates that unbeknownst to the customers, Unit 8200 and its partner NSA likely enjoyed "back door" access to the computers of clients in those and other nations. The precedence for such a strategy was in the 1980s, when INSLAW's Enhanced Prosecutors Management Information Systems (PROMIS) was stolen and re-programmed by a CIA proprietary firm, Hadron, as well as by Israel's Mossad, to permit back door access to the computers of law enforcement and intelligence agencies in dozens of countries around the world, including Singapore, Canada, Iraq, Egypt, Philippines, and Jordan. The Reagan, George HW Bush, and Clinton administrations covered up the U.S. Department of Justice's theft and misuse of the program.
Hacking Team's corporate counsel is Eric Rabe, a former senior vice president for Verizon Communications. In a phenomenal display of hubris and "chutzpah," Rabe said, "law enforcement will investigate the illegal taking of proprietary company property," even though the theft of other individuals' and companies' personal and proprietary property is how Hacking Team made its money.
What is even more troubling is the fact that the former U.S. ambassador to Italy, Ronald Spogli, a venture capitalist and Republican Party fundraiser from Los Angeles, was an investor in Hacking Team. Spogli heads INNOGEST, which has provided seed capital to Hacking Team, and is the co-founder of Freeman Spogli & Company, a U.S. investment firm. Hacking Team, the actual brainchild of two Italian programmers, Alberto Ornagh and Marco Valleri, started up operations in Milan around 2006. Spogli served as the top U.S. envoy in Rome from 2005 to 2009. Milan was also central to the Italian police investigation of the CIA station chief in that city, Robert Seldon Lady. In February 2003, Lady, a native of Honduras, and his CIA team arranged for the kidnapping of Muslim Imam Hassan Mustafa Osama Nasr, who was then renditioned to Egypt where he was tortured by Egyptian security. Lady retired in September 2003 and moved to Asti, Italy. In June 2005, Lady escaped from Italy before he could be arrested by Italian police for the kidnapping of Nasr. Lady was convicted of kidnapping in absentia by an Italian court and remains a fugitive from Italian justice. As ambassador, Spogli used his influence in Rome to stymie Italian efforts to seek Lady's extradition from the United States.

Spogli (far right) with Italian Prime Minister Silvio Berlusconi (center) and delegation of the American Jewish Committee that visited Rome in 2008. Spogli's predecessor in Rome was Mel Sembler, chairman of the Republican Jewish Coalition, the Scooter Libby Defense Fund, and Straight, Inc. The latter, now known as the Drug Free America Foundation (DFAF), is a non-profit that has been discovered to have engaged in the mental and sexual abuse of Florida youth sentenced to the group's drug treatment program. 2016 presidential candidate Jeb Bush is on DFAF's advisory board.
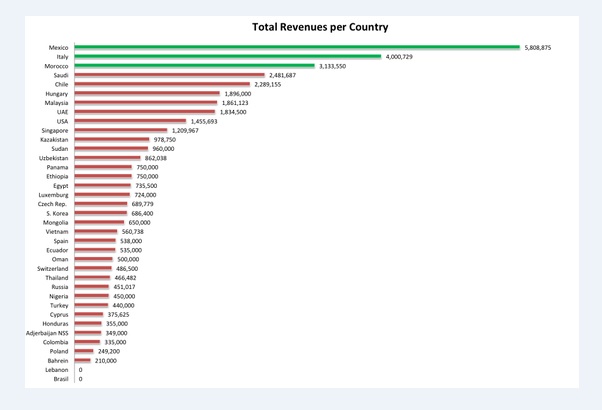
International sales of hacking software by Hacking Team, a Milan-based firm tied to Israeli intelligence. Mexico leads in sales, followed by Italy, Morocco, Saudi Arabia, Chile, Hungary, Malaysia, United Arab Emirates, United States, Singapore, Kazakhstan, Sudan, Uzbekistan, Panama, Ethiopia, Egypt, Luxembourg, Czech Republic, South Korea, Mongolia, Vietnam, Spain, Ecuador, Oman, Switzerland, Thailand, Russia, Nigeria, Turkey, Cyprus, Honduras, Azerbaijan, Colombia, Poland, and Bahrain. Zero sales to Lebanon and Brazil does not preclude the possibility that they were granted use of demonstration software. Other nations identified in hacked files as Hacking Team clients include Belarus, Kuwait, Finland, Greece, Guatemala, India, El Salvador, Turkmenistan, Kyrgyzstan, Bangladesh, Poland, South Africa, Syria, Kurdistan Regional Government, Pakistan, Estonia, and Qatar.
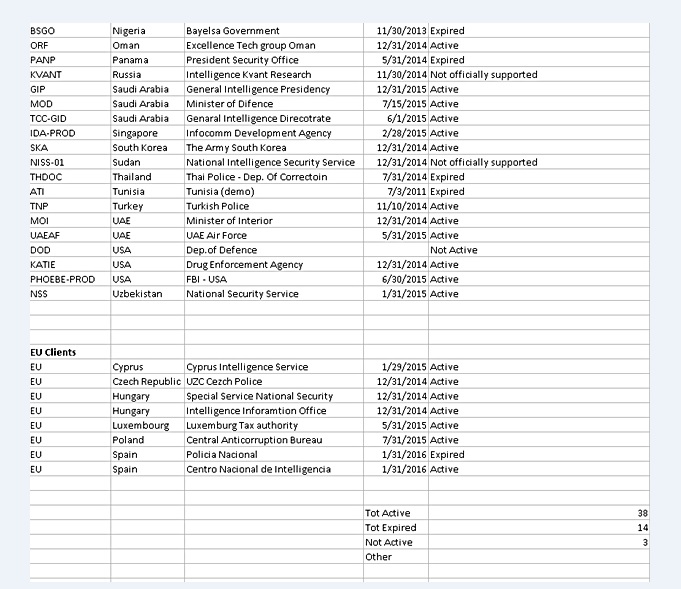
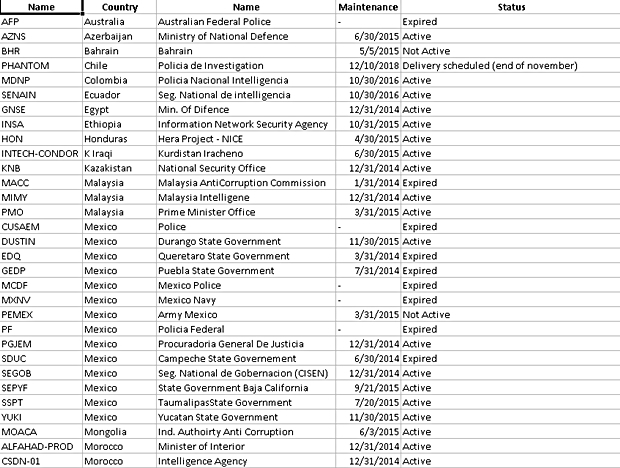
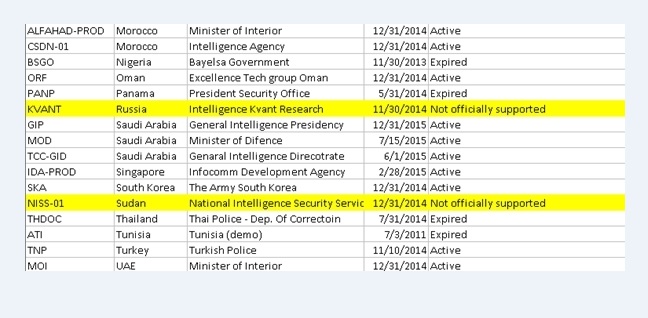
Hacking Team software was used to spy on the computer communications and files of journalists in Ethiopia and Panama.
This editor, in 1988, penned a prophetic warning about the future of an ever-growing interconnected data network world. In the 1988 edition (Volume 7, Number 4) of the academic journal "Computers and Security," an article, titled,"The World Meganetwork and Terrorism," warned ". . . there is a distinct likelihood that the international meganetwork will one day break down from terrorist sabotage. As networks become more interactive and interoperable and as terrorists become more sophisticated in their tactics, it will be incumbent on all responsible levels within the international, national and corporate community to prevent our lifelines from being disrupted by those sinister elements that seek to destroy our civilized way of life."
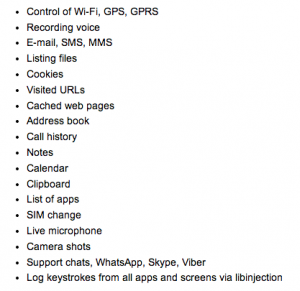
List of Hacking Team's "Remote Control System" and "DaVinci" software targets
In 1999, it became clear that the "sinister elements" included the nascent "offensive information warfare" cadres being formed by the NSA and CIA. As members of the board of directors of the International Information System Security Certification Consortium (ISC)2, myself and my Finnish colleague voiced our objections to allowing NSA a place of responsibility within the governing body that professionally certified computer security professionals around the world. By that time, NSA's goals of using computer networks for espionage and sabotage had become abundantly clear. When the rest of the board members decided to welcome NSA to the table, myself and Finnish data security expert Juhani Saari resigned our board memberships in protest. The future "sinister elements" referred to in 1988 turned out not to be evil hackers sitting at keyboards in some Middle Eastern backwater, but military and civilian personnel of the NSA, U.S. Cyber Command, and like-minded agencies. They have now been caught using privately-developed software programs, including "Remote Control System" from Hacking Team, to carry out their dangerous activities.

"Computers and Security" is the official journal of Technical Committee 11 of IFIPS, the International Federation of Information Processing Societies
As a result of counter-hacking by a "white hat" team of computer hackers, a Milan-based firm, Hacking Team, has been revealed as providing sophisticated hacking tools to the U.S. Federal Bureau of Investigation, the U.S. Drug Enforcement Administration (DEA), and intelligence and law enforcement agencies around the world, including Australia, Azerbaijan, Georgia, India, Panama, and dozens of other countries. Colombia's security agencies actually bought Hacking Team software with funds provided by the DEA.
Leaked Hacking Team documents also point to the firm's software being used to target the computer systems of ABI, Ltd. (Antigua and Barbuda), Barclays, ING Direct, Deutsche Bank, and ABN Amro.
Hacking Team also targeted the computers of Human Rights Watch and Privacy International (PI). Since 1996, this editor has served as a member of PI's International Advisory Board, as well as a contributing editor to the group.Hacking Team founder Christian Pozzi has stated that the hackers who exposed the firm's nefarious activities "will be arrested" and that the company is "working with the police at the moment." Signor Pozzi should realize that by targeting journalists in the United States and PI, it is he and his firm that could face law enforcement action if it should be determined that this editor's computer files, email, or WayneMadsenReport.com has, in any way, been subjected to hacking by his firm or any of its customers.
The presence of Hacking Team's U.S. office at 1997 Annapolis Exchange Parkway, Suite 300, in Annapolis, Maryland also suggests that the National Security Agency and its U.S. Cyber Command operation, located nearby in Fort Meade, Maryland, also used the hacking firm's products. In addition to its headquarters on Via della Moscova in Milan, Hacking Team maintains an office at UOB Plaza 1, 80 Raffles Place Level 35-25, in Singapore. In addition, there are reports that the Central Intelligence Agency was also an avid fan of Hacking Team's cyber-snooping software.

Hacking Team is also connected to Israeli intelligence. Its corporate partner, Nice Systems, Ltd., an Israeli software services firm located at 8 Hapnina Street, Raanana, Israel, was connected to some of the Israeli "art students" rounded up by U.S. law enforcement after they were found casing U.S. government facilities and private homes and offices in the months leading up to the 9/11 attack. Nice Systems employees arrested included Tomer Ben Dor (date of birth, 8/24/1975), a former Israeli Defense Force officer, and Michael Calmanovic (date of birth, 9/06/1975), the leader of the Israeli team operating out of Irving, Texas, close to Dallas-Fort Worth International Airport. The Irving team not only included employees of Nice Systems but also the telecommunications billing software firm AMDOCS. Calmanovic rented a mail drop at 3575 Beltline Road in Irving, just a few blocks from the 4045 Beltline Road residence of Almad Khafefa, one of the Saudi suspects in the 9/11 attack.
Nice Systems's chief executive officer is Barak Eilam, a former officer of Israel's signals intelligence agency and NSA's "Third Party" partner, Unit 8200. Nice's president of the Intelligence Solutions Division of the Security Group is Yossi Ofek. One of the Israeli art students arrested in the United States prior was Aran Ofek, identified by DEA as the son of a two-star general in the IDF. Aran Ofek lived with the Mossad cell at Oak Hill Apts. 1913 Estrada Parkway, #259, Irving, TX., and he was arrested by the U.S. Immigration and Naturalization Service on March 26, 2001.
Hacking Team used various code words for its American clients. The DEA was KATIE, the FBI's little-known Remote Operations Unit was called "PHOEBE," and the CIA was known as "MARIANNE." The sale of the Israeli-connected hacking software to such countries as Syria, Sudan, and Pakistan indicates that unbeknownst to the customers, Unit 8200 and its partner NSA likely enjoyed "back door" access to the computers of clients in those and other nations. The precedence for such a strategy was in the 1980s, when INSLAW's Enhanced Prosecutors Management Information Systems (PROMIS) was stolen and re-programmed by a CIA proprietary firm, Hadron, as well as by Israel's Mossad, to permit back door access to the computers of law enforcement and intelligence agencies in dozens of countries around the world, including Singapore, Canada, Iraq, Egypt, Philippines, and Jordan. The Reagan, George HW Bush, and Clinton administrations covered up the U.S. Department of Justice's theft and misuse of the program.
Hacking Team's corporate counsel is Eric Rabe, a former senior vice president for Verizon Communications. In a phenomenal display of hubris and "chutzpah," Rabe said, "law enforcement will investigate the illegal taking of proprietary company property," even though the theft of other individuals' and companies' personal and proprietary property is how Hacking Team made its money.
What is even more troubling is the fact that the former U.S. ambassador to Italy, Ronald Spogli, a venture capitalist and Republican Party fundraiser from Los Angeles, was an investor in Hacking Team. Spogli heads INNOGEST, which has provided seed capital to Hacking Team, and is the co-founder of Freeman Spogli & Company, a U.S. investment firm. Hacking Team, the actual brainchild of two Italian programmers, Alberto Ornagh and Marco Valleri, started up operations in Milan around 2006. Spogli served as the top U.S. envoy in Rome from 2005 to 2009. Milan was also central to the Italian police investigation of the CIA station chief in that city, Robert Seldon Lady. In February 2003, Lady, a native of Honduras, and his CIA team arranged for the kidnapping of Muslim Imam Hassan Mustafa Osama Nasr, who was then renditioned to Egypt where he was tortured by Egyptian security. Lady retired in September 2003 and moved to Asti, Italy. In June 2005, Lady escaped from Italy before he could be arrested by Italian police for the kidnapping of Nasr. Lady was convicted of kidnapping in absentia by an Italian court and remains a fugitive from Italian justice. As ambassador, Spogli used his influence in Rome to stymie Italian efforts to seek Lady's extradition from the United States.
Spogli (far right) with Italian Prime Minister Silvio Berlusconi (center) and delegation of the American Jewish Committee that visited Rome in 2008. Spogli's predecessor in Rome was Mel Sembler, chairman of the Republican Jewish Coalition, the Scooter Libby Defense Fund, and Straight, Inc. The latter, now known as the Drug Free America Foundation (DFAF), is a non-profit that has been discovered to have engaged in the mental and sexual abuse of Florida youth sentenced to the group's drug treatment program. 2016 presidential candidate Jeb Bush is on DFAF's advisory board.

International sales of hacking software by Hacking Team, a Milan-based firm tied to Israeli intelligence. Mexico leads in sales, followed by Italy, Morocco, Saudi Arabia, Chile, Hungary, Malaysia, United Arab Emirates, United States, Singapore, Kazakhstan, Sudan, Uzbekistan, Panama, Ethiopia, Egypt, Luxembourg, Czech Republic, South Korea, Mongolia, Vietnam, Spain, Ecuador, Oman, Switzerland, Thailand, Russia, Nigeria, Turkey, Cyprus, Honduras, Azerbaijan, Colombia, Poland, and Bahrain. Zero sales to Lebanon and Brazil does not preclude the possibility that they were granted use of demonstration software. Other nations identified in hacked files as Hacking Team clients include Belarus, Kuwait, Finland, Greece, Guatemala, India, El Salvador, Turkmenistan, Kyrgyzstan, Bangladesh, Poland, South Africa, Syria, Kurdistan Regional Government, Pakistan, Estonia, and Qatar.



Hacking Team software was used to spy on the computer communications and files of journalists in Ethiopia and Panama.
This editor, in 1988, penned a prophetic warning about the future of an ever-growing interconnected data network world. In the 1988 edition (Volume 7, Number 4) of the academic journal "Computers and Security," an article, titled,"The World Meganetwork and Terrorism," warned ". . . there is a distinct likelihood that the international meganetwork will one day break down from terrorist sabotage. As networks become more interactive and interoperable and as terrorists become more sophisticated in their tactics, it will be incumbent on all responsible levels within the international, national and corporate community to prevent our lifelines from being disrupted by those sinister elements that seek to destroy our civilized way of life."

List of Hacking Team's "Remote Control System" and "DaVinci" software targets
In 1999, it became clear that the "sinister elements" included the nascent "offensive information warfare" cadres being formed by the NSA and CIA. As members of the board of directors of the International Information System Security Certification Consortium (ISC)2, myself and my Finnish colleague voiced our objections to allowing NSA a place of responsibility within the governing body that professionally certified computer security professionals around the world. By that time, NSA's goals of using computer networks for espionage and sabotage had become abundantly clear. When the rest of the board members decided to welcome NSA to the table, myself and Finnish data security expert Juhani Saari resigned our board memberships in protest. The future "sinister elements" referred to in 1988 turned out not to be evil hackers sitting at keyboards in some Middle Eastern backwater, but military and civilian personnel of the NSA, U.S. Cyber Command, and like-minded agencies. They have now been caught using privately-developed software programs, including "Remote Control System" from Hacking Team, to carry out their dangerous activities.

"Computers and Security" is the official journal of Technical Committee 11 of IFIPS, the International Federation of Information Processing Societies
